Passwords and Users with Superpowers: Two Common Security Risks and What to Do About Them in IBM i
Connectria
Author
Date
February 18, 2020

In our previous post about HelpSystems’ annual State of IBM i Security study, we recapped one key theme the report unearths every year.
The highest points of vulnerability in data centers aren’t IBM i related. They are simply caused by human error. IBM i is highly securable when protocols are enforced to secure it.
Breaches happen when a lack of standardizations, automation, and sensible oversight fail to protect critical data. The most common threats also happen to be the most avoidable.
In this article, we examine how super users (users with access to too many systems with a single authentication) and simple password settings, when left unmanaged, could lead to data breaches. Unmonitored, those simple settings could point to a lost security opportunity for firms that don’t follow defined password security protocols or simply fail to manage them.
The Potential Threat Posed by Users with Unrestricted System Access
The systemic failures that most commonly result in security breaches are rooted in human behavior and company culture. Whether through negligence or actual malicious intent, users with overreaching authority across too many databases and directories can pose serious security threats. This includes admins.
At the very least, even the most cautious of users can mistakenly download malware. The worst-case scenario would be an admin with an ax to grind with your company or one that is excessively careless and retains system access long after their departure.
When a user with administrative privileges erroneously imports phishing software, that could make data like customer credit card information, employee records, and other secret information accessible to criminals.
So, what’s the solution? If you have IBM i architecture, you can simply implement IBM i’s existing special authorities to limit the users who have special authorities. Then put in place a process to monitor those users carefully so that the worst-case scenario is less likely to happen.
Best practices for such a process include:
- Limiting the users with special authority to fewer than 10. A good rule of thumb is to keep this number to less than 3 percent of the user community.
- Maintain and update proper documentation to enforce the separation of duties for users with powerful authorities.
- Avoid establishing users that retain powerful authentications across all systems.
- Keep a regular record and log the use of those powerful authorities.
- Create a chain of reporting for auditors and managers to retain and protect transparency.
- Ensure that admins are accountable for their activities and establish audits and review for all admin behavior.
Problems with Passwords and Inactive Profiles
In most IT arenas, it’s not uncommon, for staff to be resistant to time-consuming documentation. But a standardized documentation process is critical to maintaining data integrity.
If you don’t have password security standards in place, all the other security measures you’re taking might not matter.
Accounts that haven’t been used for 30 days or more are especially ripe for hacking. Inactive profiles belonging to former employees or contractors are equally vulnerable. If securing data is your objective, then the last thing any company needs is a former consultant working for a competitor who has full access to your directories.
An ex-employee stops monitoring their account once they walk out the door. They will never know if anyone else is using their inactive profile. Login or other activity will go unreported, and you may not know that an inactive account has been used to hack your files until it’s too late.
Of the systems audited for the HelpSystems report, inactive profiles showed some of the biggest areas for improvement:
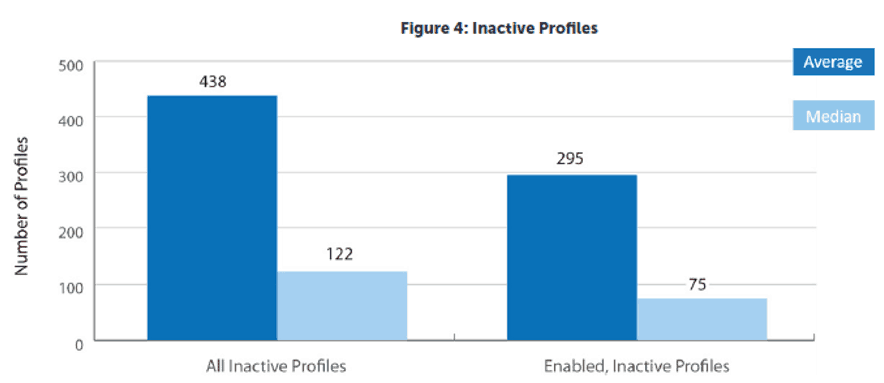
Thirty-six percent of the average 438 profiles sampled were not used in 30 days or more. Of those, 295 had an active status.
Solution: IBM i has both manual and automated solutions to manage and monitor inactive profiles. They won’t do you much good, however, if you don’t have a standardized and monitored methodology in place to use them. So, define and develop a protocol for inactive profiles and users.
Establish regular audits to flag any profiles that haven’t been used for a certain period of time (30 days, 45 days, etc.). Enact and automate rules to manage those inactive profiles, including removing authorities. You could also establish a wait period of an additional 30 days to confirm the profile is truly inactive before you permanently delete it.
Bottom line: Make sure the process you develop falls in line with your company’s culture. Follow any steps necessary to keep audit trails intact. With the proper oversight, your team can utilize IBM i’s existing solutions that satisfy your business climate without ignoring the dangers that inactive profiles can cause.
Define, Manage, and Implement Common-Sense Password Security Measures
IBM i has a set of password defaults (the username and the password are the same). The report found a prevalence of default passwords still in place, which makes guessing passwords incredibly intuitive and easy for users with a history and knowledge of IBM i.
Establish password policies that specifically make it more difficult to compromise network security. At the very least, put measures in place to force all users to update default passwords.
Automatic password expiration periods (90 days is a good rule of thumb) ensures that exiting users, like contractors and temp staff, do not have unlimited access after they stop working for you. The systems studied had an average password interval of 95 days, and we concur that a password expiration interval is crucial.
Standards for Minimum Password Length
Best practices are 8 characters or more, but only 41 percent of those surveyed meet those standards. Nearly 60 percent of the servers in the study failed to satisfy a minimum of 7-character passwords, and 98 percent did not pose restrictions on characters.
Note that IBM i introduced QPWDRULES with V6.1. That system allows managers to designate password policy settings in a single repository. As with the other security features uncovered in the study, the system itself allows for best practices, but users are failing to utilize them.
Your sys admins need to establish automated and sensible password expiration policies. The study, by way of example, revealed that of the clients they audited, 54 percent do not require a digit in passwords, resulting in common words or alpha-only (weak) passwords.
Also, put automated notifications and locks in place in the event of failed login attempts. Your company will be the most protected when a profile is disabled or locked if the maximum login attempts are exceeded. IBM i also allows for multi-factor authorization or asking for one more credential in addition to the username and password.
Build Guidelines that Suit Your Culture
There is no one-size-fits-all solution for every business environment. IT managers may be reluctant or opposed to putting limitations on super users or admins with unrestricted access with a single authentication. The more automation that is in place, the more audit trails and documentation are cemented into your workflow, the easier it is to safeguard your customer and company data.
Most facility security policies all but guarantee that an ex-employee can’t gain access to your building or a floor using an expired key card. Your databases and client records need just as much protection as your physical facilities.
Often, a retiring IBM i admin walks out the door with their knowledge locked inside their head. This means that team leaders are unaware of all of the daily activities of admins, and when those key employees leave the company, it’s not uncommon that their knowledge base and daily routines leave with them.
Documentation and audits are both time-consuming and most of your staff is busy with day-to-day duties. However, waiting for an employee to announce a departure is the worst time to document that person’s workflow.
Third-party cloud management not only ensures improved auditing, reporting, and security, it also provides continuity and redundancy. An experienced team with deep knowledge of existing legacy infrastructure and newer data management strategies ensures seamless operations for staff and customers as well as needed redundancy.
Learn more on our IBM i platform services information page.
Topics
Keep Reading
Prepare for the future
Tell us about your current environment and we’ll show you the best path forward.
Fast track your project. Give us a call.